
Securing Your App : Best Practices In Mobile Application Development
Written by: Shiva kumaran
Quick Summary
We all know how tedious it is to translate your idea into an App reality. Thousands of hours must have gone into the development process - brainstorming, coding, testing, and refining - to create an application that stands out from the rest and offers real value to its users. And after spending sleepless nights and thousands of iterations later, you finally launched your App!
Congratulations on this moment of triumph, and it’s well-deserved! However, in the midst of celebrating, it’s crucial not to forget about something vital: the security of your hard-earned creation. A successful breach can lead to severe consequences, including damage to your reputation, legal issues, financial losses, and most importantly, loss of trust from your users. So, it’s essential to prioritize app security and ensure your success remains unblemished.
But worry not! When it comes to Mobile Application Development ↗, knowing the best practices to maintain app security really helps. This comprehensive guide is your go-to resource to fortify your app’s defenses and navigate the ever-evolving landscape of app security. Emphasizing a proactive approach, we will equip you with the knowledge and best practices to safeguard your app and its users from potential threats.
Let’s dive in!
Why App Security Matters
Consider this: In 2023, the average global cost associated with a data breach soared to an eye-watering $4.45 million, marking a 15% increase over a mere three-year span. This statistic is a stark reminder of the escalating risks in our increasingly digital world, where app usage is surging like never before.
In this context, app security is not just an option; it’s an absolute necessity. It’s akin to the lock on your front door, safeguarding your most valuable assets. If this security is compromised, the fallout can be catastrophic, leading to data breaches, identity theft, and financial fraud.
Prioritizing app security is a testament to your commitment to protecting user data, a move that earns their trust. It’s also a crucial step in maintaining your brand reputation and adhering to regulatory guidelines like GDPR and CCPA.
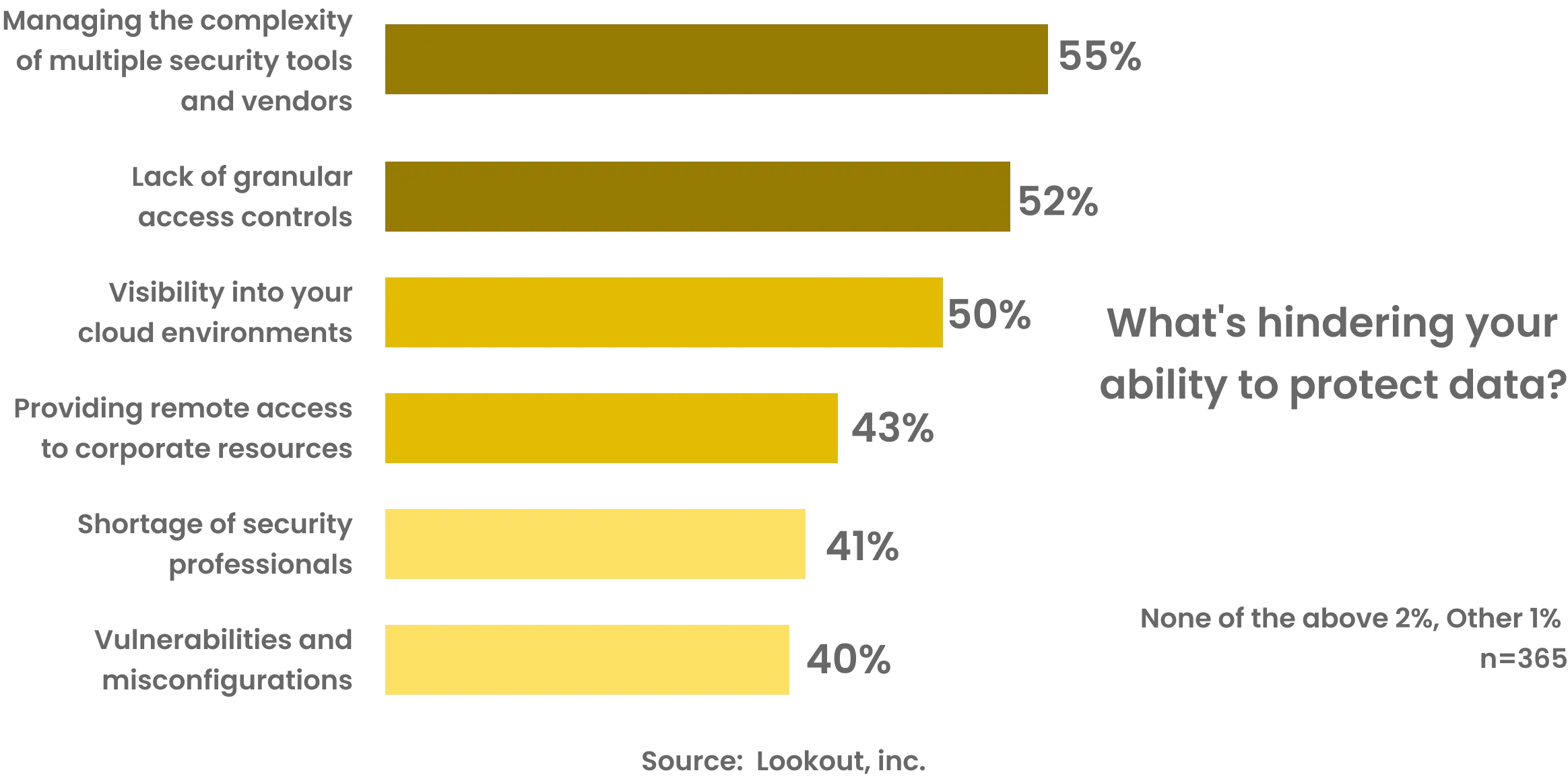
Securing Your App: A Layered Approach
Think of securing an app as a complex puzzle. It involves multiple interconnected pieces, each playing a crucial role in creating a complete picture of security. These pieces are interconnected, and a weakness in one can affect the others. In Mobile Application Development, you need to approach the security aspects one layer after the other. Let’s explore these integral pieces of the app security puzzle:
Front-End Security
The front end of your app is the user interface, the part of your app that users interact with. It’s crucial to secure this layer as it’s the first line of defense against potential threats. Embracing secure coding practices from the get-go can fortify your app’s defenses. One of these practices is input validation, which acts as a gatekeeper, ensuring only the right kind of information gets through.
Now, you might be wondering, what kind of threats are we talking about? Well, let’s take a look at two common ones: SQL Injection and Cross-Site Scripting (XSS). SQL Injection is a code-based vulnerability that allows an attacker to sneak a peek into your database, reading and accessing sensitive data. Imagine a user input field on your app asking for a user’s ID. An attacker could input a tricky command that confuses the system into revealing more data than it should.
On the other hand, XSS occurs when an attacker sneaks a harmful script into a trusted website, just like slipping a harmful note onto a public message board. By validating user inputs, you ensure that these malicious commands are detected and neutralized before they can cause any harm.
A real-world example of a front-end security breach is the 2016 attack on Yahoo, where hackers used a spear-phishing email to gain access to Yahoo’s internal networks. The breach affected about 500 million users, making it one of the largest in history
By implementing strong authentication protocols and prevention code from the start, you can protect your app against such ‘injection attacks and other potential threats.
Back-End Security
The back end of your app is like the control room of a spaceship. It’s where all the data processing happens, the engine that powers your app, and it’s vital to secure it. This is where the data from the user inputs gets processed, transformed, and stored. It’s the heart of your app’s functionality, and any vulnerability here can have serious consequences.
To secure the back end, you need to implement secure APIs. APIs, or Application Programming Interfaces, are like the communication channels between different software components. They allow your app to interact with other apps and services. However, if not secured properly, they can become a gateway for attackers to infiltrate your app.
When it comes to Mobile Application Development another crucial aspect of back-end security is using secure server configurations. This involves setting up your servers in a way that minimizes vulnerabilities and potential attack vectors. Regular patching is also essential, as it helps fix any known vulnerabilities that could be exploited by attackers.
During the Equifax breach, a vulnerability in their web application framework led to the exposure of personal information belonging to 147 million people. Attackers exploited this weakness to gain unauthorized access and steal sensitive data.
The 2017 Equifax, a major credit reporting agency, suffered a massive breach that exposed the personal information of 147 million people. The breach was a result of a vulnerability in a web application framework it used. The attackers exploited this vulnerability to gain access to the company’s systems and steal sensitive data
This incident serves as a stark reminder of the potential consequences of neglecting back-end security. By implementing secure APIs, using secure server configurations, and regularly patching your systems, you can significantly enhance the security of your app’s back end.
Cloud Security
The cloud is like a vast digital warehouse, storing and managing data for countless apps. If your app uses cloud services ↗ for data storage or processing, it’s akin to storing your app’s valuable assets in this warehouse. Just as you would ensure the security of a physical warehouse, you need to ensure that these cloud services are secure.
Cloud security involves several key practices. First, you need to use secure cloud configurations. This is like setting up the right security measures in your warehouse, such as CCTV cameras and alarm systems. Misconfigurations can leave your data exposed, much like leaving a warehouse door unlocked.
Next, you need to encrypt data at rest and in transit. Encryption is like a secret code that scrambles your data, making it unreadable to anyone who doesn’t have the decryption key. Encrypting data at rest protects it while it’s stored in the cloud while encrypting data in transit protects it while it’s being transferred from one place to another.
Finally, implementing robust access controls is crucial. This is like having a strict access policy for your warehouse, ensuring only authorized personnel can enter. In the context of cloud security, this means controlling who can access your data and what they can do with it.By investing in Cloud Application Development Services ↗, you can ensure that your app is not only functional but also secure and resilient in the cloud environment.
The 2019 Capital One data breach, where a misconfigured web application firewall on AWS led to the exposure of 106 million customer records, highlights the importance of cloud security
Battling Bots
In the digital world, bots can be like unwanted visitors causing trouble for your app. Some bots are harmless and used by search engines to index web pages, while others are malicious. These malicious bots can scrape content, try to access your app with stolen credentials, and even launch attacks to make your app unavailable. It’s important to protect your app from these bots to keep it secure and stable.
Bots can pose a significant threat to your app. They can scrape content, copying, and republish it without your permission. This can harm your app’s SEO rankings, lead to the loss of unique content, and even result in legal issues if the scraped content is copyrighted.
Credential-stuffing attacks are another common threat posed by bots. In these attacks, bots use stolen usernames and passwords to try to gain access to user accounts. If successful, they can lead to data breaches, identity theft, and financial fraud.
To protect your app from these threats, it’s crucial to implement bot management solutions. These solutions can help you distinguish between human users and bots, allowing you to block malicious bots while letting good bots through. They work like a bouncer at a club, checking each visitor (or in this case, each request to your app) and deciding whether to let them in based on a set of rules.
In 2017 both the UK and Scottish Parliaments fell victim to brute-force attacks, while a similar but unsuccessful attack occurred on the Northern Irish Parliament a year later. Airline Cathay Pacific suffered a brute force attack a year later for which it was fined ~$630,000 by the UK’s data regulator due to lacking sufficient preventive measures
This incident is a strong reminder of the damage that bots can cause if not controlled. By using effective bot management solutions, you can protect your app from harmful bots and ensure a safe and smooth user experience.
Enhanced User Authentication
Strong user authentication is a crucial part of app security. It goes beyond just having a password; it involves techniques like multi-factor authentication, biometric authentication, and the use of strong, unique passwords.
Let’s break it down a bit. Multi-factor authentication (MFA) is a method where a user is granted access only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism. These factors could include something they know (like a password), something they have (like a hardware token or a phone), and something they are (like a fingerprint or other biometric data).
Biometric authentication, on the other hand, uses unique biological characteristics like fingerprints, facial recognition, or iris scans to verify a user’s identity. This method is becoming increasingly popular due to its high level of security and ease of use.
Strong, unique passwords are also an essential part of user authentication. Encouraging users to create complex and unique passwords for their accounts can significantly reduce the risk of unauthorized access.
In 2012, LinkedIn suffered a significant data breach where 6.5 million hashed passwords were stolen and posted on a Russian hacker forum5. The breach was a result of LinkedIn not salting their passwords (a method of extra secure hashing). This incident underscores the importance of implementing strong user authentication methods.
However, it’s not just about having these methods in place. It’s also crucial to keep them updated and to educate users about the importance of using them correctly. For instance, users should be aware of the risks of sharing their authentication information and the importance of keeping their biometric data secure.
By implementing and maintaining strong user authentication methods, you can significantly reduce the risk of unauthorized access to your app, protecting both your users and your reputation
Server-Side Security
The server side of your app is akin to the backstage crew at a theater performance. It’s where all the behind-the-scenes action happens, and it’s crucial to keep this area secure. Server-side security involves securing the servers that your app relies on, and it encompasses a variety of techniques.
Regular patching is one such technique. Just like you’d patch a hole in a boat to prevent it from sinking, you need to regularly patch your servers to fix any security vulnerabilities that could be exploited by attackers. This involves keeping your server software up-to-date and applying any security patches released by the software provider. Remember these things in Mobile Application Development as they play a vital role .
Using secure configurations is another important aspect of server-side security. This involves configuring your servers in a way that minimizes the risk of a security breach. For example, you should disable any unnecessary services, limit the number of privileged users, and use firewalls and intrusion detection systems to monitor and control incoming and outgoing network traffic.
Monitoring for any signs of intrusion is also crucial. This involves keeping an eye on your server logs and using intrusion detection systems to alert you of any suspicious activity. If an intrusion is detected, you should have a response plan in place to mitigate the impact and prevent further damage.
To illustrate the importance of server-side security, let’s take a detour into a real-life incident. Shorebreak Security reported an instance where a Server-Side Request Forgery (SSRF) attack exploited a vulnerability in a commercial Business Intelligence product called Dundas BI. The attacker manipulated the application to issue requests to unintended resources on their behalf. Thankfully, the vendor has since patched this vulnerability, underlining the importance of regular patching and proactive security measures
By implementing robust server-side security measures, you can protect your app from the backstage, ensuring a smooth and secure performance for your users.
Conclusion
In conclusion, securing your app is a complex, ongoing process that involves multiple layers of defense. By understanding the threats you face and implementing the best practices outlined in this guide, you can help protect your app and its users from potential threats. Remember, in the world of app security, a proactive approach is always the best defense. Having a team of dedicated developers ↗ by your side can make a significant difference. Why search elsewhere when you have us? Reach out today to learn more.



